
How can you conquer the most common security risks with OTP authentication?
OTP (One-time password) Integration for Developers
Even though we live in the century of technological disruption, surprisingly enough recent research shows that 42% of organizations still rely on sticky notes to manage their passwords, whereas 59% of IT professionals state that the companies they work for, depend on human memory to manage passwords. Facts that -combined with the substantial evolution of cybercrime where data breaches become prevalent and privacy concerns intensify- lead to the reasonable conclusion that software developers have a difficult task in fortifying their websites, platforms, and applications.
Relying on a simple password to prevent data loss is not just a totally outdated method, but it turns out to be a highly vulnerable way as well that can lead to extremely costly data breaches.
In the past few years, data breaches have become a major pressure point for businesses and developers worldwide. In 2019, approximately 80% of data breaches resulted from password compromise. Hence, consumers have become more aware and selective with the businesses, websites, platforms, and apps that they choose for their monetary transactions and data safeguarding. Software developers need to shift their focus from building systems that are just password-protected to developing integrated systems that incorporate identity verification and access authentication management solutions.
Especially now that the business demand for mobile applications is high and growing, mobile app developers must include in their project checkboxes the feature of enhanced security, apart from an enticing UI/UX functionality.
What are the most common security risks faced in authentication?
Let us take a quick look at the most common security risks that developers have to take into consideration before integrating a comprehensive authentication process into their system, app, or platform.
Storing user credentials without encrypting them.
Even if you prompt users to change their password as soon as they complete their sign-up, or if their password has been exposed, people tend to apply the same password again, and in most cases just a plaintext password.
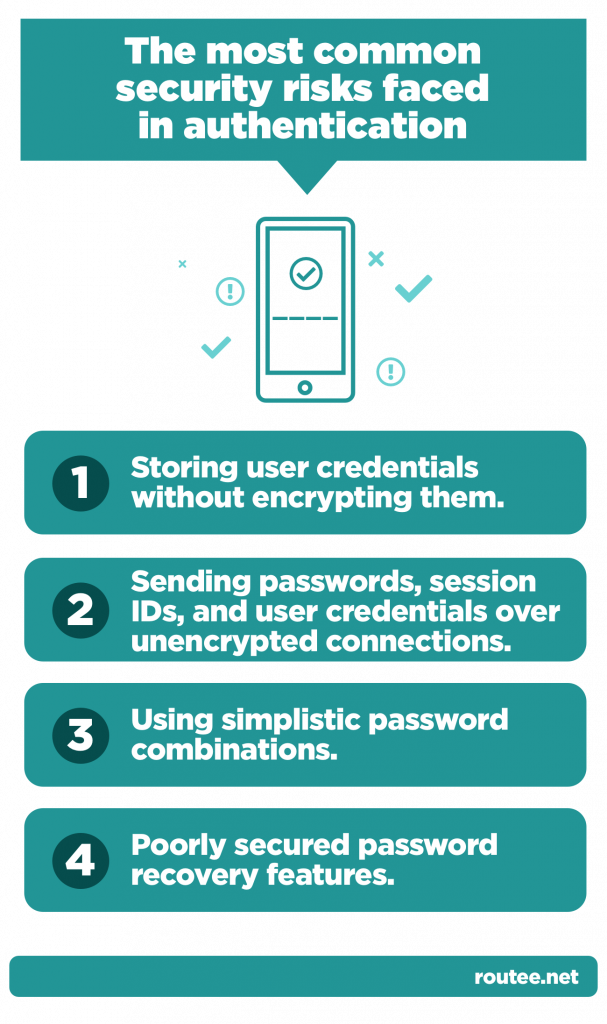
Sending passwords, session IDs, and user credentials over unencrypted connections.
Not all companies employ encrypted server-to-server and server-to-client transmissions for their communications, leaving their sensitive transactions vulnerable to attackers. Anyone with access to the connection itself can monitor and hijack the credentials.
Using simplistic password combinations.
Users tend to use simplistic passwords that they can easily remember. However, these passwords can be cracked in a few seconds by any hacker that has access or knows how to use a password-cracking tool easily found online.
Poorly secured password recovery features.
As users tend to use simplistic passwords to sign up on apps and websites, they will do so in case they need to recover their passwords. And in this case, many companies lack strong authentication procedures. Even if a business employs security questions, anyone who is familiar with the specific user can answer these questions.
How can developers securely reinforce user identity verification and authentication access?
Here is where OTP authentication comes to the rescue! Developers can substitute traditional passwords with OTPs or they can fortify an existing authentication process that they already deploy by transforming it to a two-factor (2FA) or multi-factor authentication (MFA) approach. In fact, developers can apply one-time password authentication to any mechanism that they need to build for identifying a user or authenticating a process, or granting access.
With the help of OTP Traffic, you can tackle all the above-mentioned security shortcomings and numerous more that derive from static password-based authentication from happening.
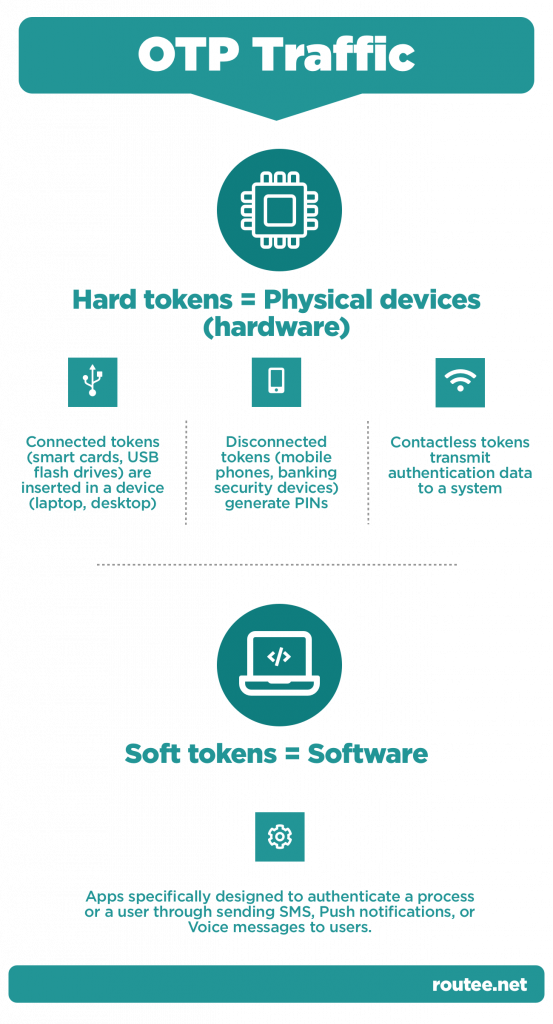
What does the secure OTP traffic consist of and how can it help developers?
As a developer, you will most probably come across different types of OTP traffic, mainly in the form of hard tokens and soft tokens.
Hard tokens are the physical devices -the hardware- that transmits one-time passwords and enable users to access their accounts. Hard tokens are broadly classified into three main sub-categories: the connected, the disconnected, and the contactless tokens.
The connected tokens are nothing more than smart cards and USB flash drives that a user must insert into a device or USB port, respectively. The disconnected tokens on the other hand come in the form of mobile phones or banking security devices and are the ones that generate OTPs for users to enter in a multi-factor authentication process. Last but not least, the contactless tokens are the ones that do not require a physical connection or a manual input. They transmit authentication data to a system which in turn, analyzes the information and identifies if the user has access rights.
Soft tokens come in the form of software that is installed in a device (e.g., laptop or smartphone). So, practically soft tokens are apps specifically designed to authenticate a process or a user through sending SMS, Push notifications, or Voice messages to users. Users have to respond to verify their identity.
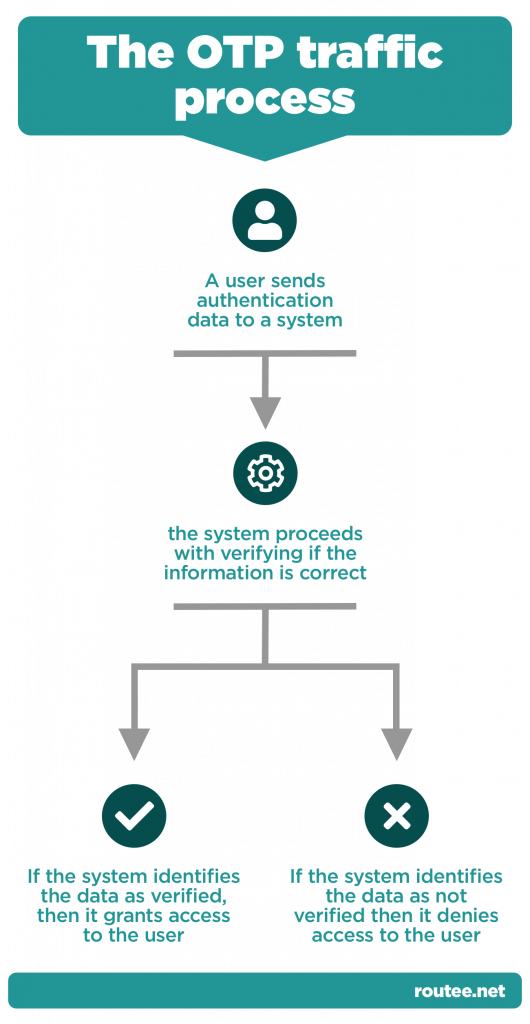
Regardless of the type of OTP traffic a developer decides to implement, the process remains the same:
1. a user sends authentication data to a system
2. the system proceeds with verifying if the information is correct
a. If the system identifies the data as verified, then it grants access to the user
b. If the system identifies the data as not verified then it denies access to the user
The major advantage of OTP authentication is that the authentication data is not transmitted beyond the user and the target system, so it cannot be leaked as it can happen with a simple password.
How can you implement a one-time password service?
Luckily, there are certain intelligent solutions in the market that allow you to easily implement and configure a reliable OTP service using web APIs. As soon as a user registers with the API you have selected for your development project, you can instantly implement two-factor authentication (2FA) and use communication channels like SMS or Voice to send over a one-time password. With next-generation verification APIs, like Routee’s, you can even deploy the generation of soft tokens without the need for wireless connectivity, such as offline TOTP codes. This way, not only you can ensure that a user has access to the correct telephone number but even to the right trusted device.
TIP
The integrated failover functionality allows you to provide an extra level of assurance for your users, as they can rest assured that they will receive the generated OTP at any of the other channels they have enabled (Viber, WhatsApp, Voice, SMS, Missed Call, Push notification, etc.)
The API’s flexibility allows you even to override the default behavior in your application UI and select to send the OTP code through a specific channel always.
Final thoughts
Soon, security will act as one of the differentiating and competing factors in the digital world, with customers and businesses preferring secure apps, systems, and platforms to maintain the privacy of their data over other online or non-digital solutions. Make sure you have your projects authentication-ready!
